One topic that seems to get overlooked is MS Outlook’s “Safe Senders” list. Recently I was asked about whitelisting a perspective email address that was expected to be going to send important emails. I suggested using Outlook “Safe Senders”
What it is and How it Works
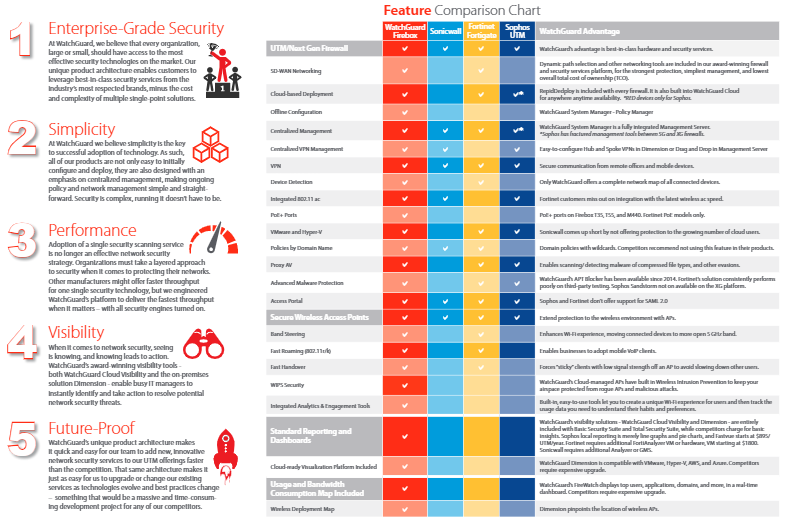
When you receive an email from someone and you right-click on the header you will get a list of selections…
When you select “Add Sender to Safe Senders List” the email address from the sender is placed in a special address list. All emails received are compared to that list and if found they will automatically go to your inbox. Think of it as your personal “Whitelist”.
But, what if you add someone and you didn’t mean to? Where is your “Safe Sender” List?
If you happen to mistakenly add someone to the list or wanted to check or update “your safe sender” list click on your junk settings. I’m using Office 365 desktop, other desktop versions of outlook are similar. Click on the “Junk Settings” button.
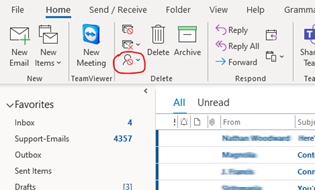
Here are the selections after you select the toolbar “Junk” button. Select “Junk E-mail Options…”
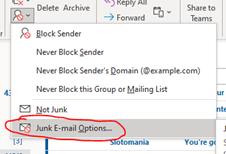
A dialog box will pop up, select “Safe Senders” on the tab bar.
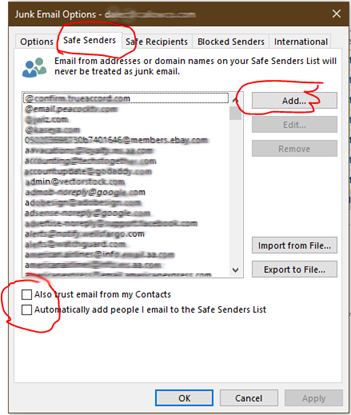
From this dialog box, you can “Add”, “Edit” and “Remove” the addresses in your “Safe Sender” list. A few other selections are “Also trust email from my Contacts” and “Automatically add people I email to the Safe Senders List. You can also Import or Export to a file.
Conclusion
Our email has certainly proved to be the basic communication standard in modern times and features like “Safe Sender” in Outlook is an unsung hero in managing our email senders. If you would like to hire me for a project, or need IT support I have plans and features available for any size business. Happy computing!